How to Detect & Fix SSRF in Java
Introduction
Server-Side Request Forgery (SSRF) is a critical web application vulnerability that can lead to unauthorized access, data leakage, and compromise of internal systems. In this article, we will delve into the detection and mitigation of SSRF vulnerabilities in Java applications. We will provide comprehensive examples, address different approaches to fix them, and highlight the impact of SSRF on compliance audits and industry standards.
Understanding SSRF
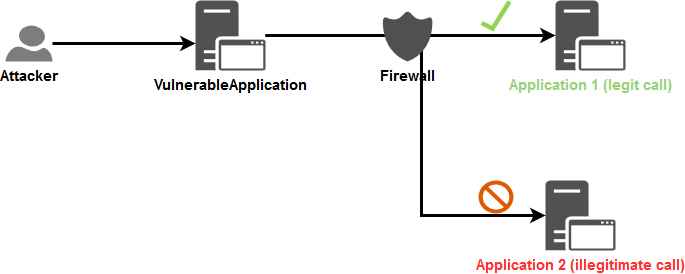
SSRF occurs when an attacker manipulates a server into making unintended requests to internal or external resources. This vulnerability arises due to insufficient input validation or insecure coding practices, allowing attackers to bypass firewalls and gain unauthorized access to sensitive data or systems.
Impact of SSRF
The impact of an SSRF vulnerability can be severe:
- Unauthorized data access: Attackers can abuse SSRF to retrieve sensitive data from internal systems, such as databases, file servers, or cloud services.
- Service disruption: SSRF can cause denial-of-service (DoS) attacks by overwhelming external systems with requests, impacting their availability.
- Remote code execution: By leveraging SSRF, attackers can execute arbitrary code on internal systems, leading to further compromise or lateral movement within the network.
Scenarios and Industry Standards
SSRF vulnerabilities are a common concern across industries and are listed in industry standards such as OWASP and SANS Top 25 Most Dangerous Software Errors. Compliance audits, such as the Payment Card Industry Data Security Standard (PCI DSS) and General Data Protection Regulation (GDPR), emphasize the need for protecting against SSRF and other web application vulnerabilities.
Detecting SSRF Vulnerabilities
- Identify user-controlled inputs: Look for inputs, such as URLs, IP addresses, or file paths, that are processed or used in requests originating from the server.
- Check for URL validation: Review how URLs are validated before being used in requests. Common flaws include weak or missing URL validation routines, which can lead to SSRF vulnerabilities.
- Analyze request patterns: Identify code patterns that indicate server-side requests, such as the use of HTTP client libraries like Apache HttpClient or Java’s
URLConnectionclass. - Review external resource usage: Examine code that fetches external resources based on user inputs, including API calls, file downloads, or remote content retrieval.
Example Vulnerable Source Code
Consider the following Java code snippet vulnerable to SSRF:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
import java.io.BufferedReader;
import java.io.IOException;
import java.io.InputStreamReader;
import java.net.URL;
public class SSRFExample {
public static void main(String[] args) {
String url = args[0];
try {
URL resourceUrl = new URL(url);
BufferedReader reader = new BufferedReader(new InputStreamReader(resourceUrl.openStream()));
String inputLine;
while ((inputLine = reader.readLine()) != null) {
System.out.println(inputLine);
}
reader.close();
} catch (IOException e) {
e.printStackTrace();
}
}
}
In this code, the user-supplied URL is used directly in the URL class without any validation or sanitization.
Mitigating SSRF Vulnerabilities
- Implement strict input validation: Validate user-supplied URLs to ensure they conform to expected patterns. Leverage libraries or regular expressions to enforce proper URL formats, including whitelisting or blacklisting certain domains.Here’s an example of secure source code that validates the URL using regular expressions:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
import java.util.regex.Matcher;
import java.util.regex.Pattern;
public class SSRFExample {
public static void main(String[] args) {
String url = args[0];
String pattern = "^(https?|ftp)://[^\s/$.?#].[^\s]*$";
Pattern urlPattern = Pattern.compile(pattern);
Matcher matcher = urlPattern.matcher(url);
if (matcher.matches()) {
// Perform further processing
try {
URL resourceUrl = new URL(url);
BufferedReader reader = new BufferedReader(new InputStreamReader(resourceUrl.openStream()));
String inputLine;
while ((inputLine = reader.readLine()) != null) {
System.out.println(inputLine);
}
reader.close();
} catch (IOException e) {
e.printStackTrace();
}
} else {
System.out.println("Invalid URL");
}
}
}
- Apply a whitelist approach: Maintain a whitelist of allowed external resources and validate user-supplied URLs against this list. Only fetch resources explicitly allowed, preventing access to internal or unauthorized resources.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
import java.net.URL;
import java.util.Arrays;
import java.util.List;
public class SSRFExample {
private static final List<String> allowedDomains = Arrays.asList("example.com", "api.example.com");
public static void main(String[] args) {
String url = args[0];
try {
URL resourceUrl = new URL(url);
String host = resourceUrl.getHost();
if (allowedDomains.contains(host)) {
// Perform further processing
BufferedReader reader = new BufferedReader(new InputStreamReader(resourceUrl.openStream()));
String inputLine;
while ((inputLine = reader.readLine()) != null) {
System.out.println(inputLine);
}
reader.close();
} else {
System.out.println("Access denied");
}
} catch (IOException e) {
e.printStackTrace();
}
}
}
- Utilize URL parsers: Instead of relying on simple string manipulation, use built-in URL parsing libraries provided by Java, such as the
java.net.URLclass. These libraries handle edge cases and ensure proper validation of URL components.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
import java.net.URL;
import java.net.MalformedURLException;
public class SSRFExample {
public static void main(String[] args) {
String url = args[0];
try {
URL resourceUrl = new URL(url);
// Perform further validation and processing
BufferedReader reader = new BufferedReader(new InputStreamReader(resourceUrl.openStream()));
String inputLine;
while ((inputLine = reader.readLine()) != null) {
System.out.println(inputLine);
}
reader.close();
} catch (MalformedURLException e) {
System.out.println("Invalid URL");
} catch (IOException e) {
e.printStackTrace();
}
}
}
- Implement network-level protections: Employ firewalls or proxy servers to restrict outbound requests from the application server. Configure these security measures to block requests to sensitive or internal IP addresses.
Java Libraries for SSRF Mitigation
While Java doesn’t have specific libraries dedicated solely to SSRF mitigation, you can leverage existing libraries and frameworks to enhance the security of your applications:
- OWASP Java Encoder: This library provides comprehensive encoding routines to prevent common web application vulnerabilities, including SSRF. It offers protection against various injection attacks and helps ensure secure handling of user-controlled inputs.
- Apache HttpClient: When making HTTP requests, consider using the Apache HttpClient library instead of directly manipulating URLs. It provides advanced features, including support for authentication, connection pooling, and request/response customization, while incorporating security best practices.
- Spring Security: If you are using the Spring framework, Spring Security offers numerous features and modules to secure your Java web applications. It provides protection against common vulnerabilities, including SSRF, through its robust authentication and authorization mechanisms.
WAF Rules:
- Implement a Web Application Firewall (WAF) that includes rules specifically designed to detect and block SSRF attacks. WAFs can analyze incoming requests and block those that exhibit SSRF patterns.
- Configure WAF rules to inspect the request headers, parameters, and payloads for SSRF indicators, such as internal IP addresses or URLs with private network ranges.
- Leverage threat intelligence feeds and regularly update your WAF rules to stay protected against the latest SSRF attack vectors.
Cloudflare Protection:
- If you are using Cloudflare as a CDN and security provider, take advantage of the security features they offer.
- Enable the “WAF” feature provided by Cloudflare to detect and mitigate SSRF attacks. Configure the WAF rules to block requests that match SSRF patterns.
- Utilize Cloudflare’s Firewall Rules to create custom rules that specifically target SSRF vulnerabilities. For example, you can create a rule to block requests containing specific headers commonly abused in SSRF attacks.
- Leverage Cloudflare’s Threat Intelligence to receive real-time threat data and enhance your protection against known SSRF attack sources.
Monitoring and Prevention Tips:
- Implement comprehensive logging mechanisms to capture and analyze server-side requests. Monitor logs for suspicious activities, such as requests to internal or unauthorized resources.
- Regularly review and update your application’s access control mechanisms. Limit the permissions of the server-side components to minimize the impact of potential SSRF attacks.
- Use network-level protections such as firewalls and network segmentation to restrict direct access to sensitive internal resources from publicly accessible servers.
- Regularly update and patch your server-side components and dependencies to address any known vulnerabilities that could be leveraged for SSRF attacks.
- Educate developers and conduct security training to raise awareness about SSRF vulnerabilities and best practices for secure coding.
By implementing WAF rules, leveraging Cloudflare’s protection features, and following monitoring and prevention tips, you can significantly reduce the risk of SSRF vulnerabilities and enhance the security of your web application.
SSRF and Compliance Audits
SSRF vulnerabilities can have implications during compliance audits. Organizations adhering to standards such as PCI DSS, GDPR, or industry frameworks like NIST Cybersecurity Framework are expected to address SSRF and web application vulnerabilities to ensure the protection of sensitive data and compliance requirements.
Conclusion
Detecting and mitigating SSRF vulnerabilities during the early coding cycle is crucial for maintaining the security of web applications. By identifying user-controlled inputs, validating URLs, implementing input sanitization, and adopting network-level protections, developers can significantly reduce the risk of SSRF attacks. Awareness of SSRF’s impact on compliance audits and adherence to industry standards further reinforce the need for thorough vulnerability mitigation practices.
